FFG: Android RPG ‘Shadow of the Beanstalk’ Setting Preview

Fantasy Flight Games might not have the rights to the Android: Netrunner Card Game – but they still have the rights to make awesome RPG content in one of the best Sci-Fi settings ever imagined. Check out what’s coming soon with Shadow of the Beanstalk, an Android RPG Campaign Guide.
It was a shame to see Android: Netrunner get the plug pulled. It was honestly one of the best competitive LCGs out there and it was a real bummer that the licensing deal ended between FFG and Wizards of the Coast. That said, FFG still has the rights to print stories and can expand it’s RPG system using the Android IP. And what an IP it is!
Android is a massive setting that involves all your favorite Cyber-punk themes – from lowtech thugs on the streets, to high powered Mega Corps and bio-tech Androids, and everything in between. The setting also incorporates locations from all over the world of Netrunner – and beyond! Honestly, it can be a little overwhelming when you start to think about it. Thankfully, FFG has a new Campaign Setting guidebook to help GMs and Players get acquainted with Android in all it’s amazing potential.
“The Net is the most prolific technology in New Angeles, and those who can manipulate or defend it hold untold power. Join us today as we preview the rules for running the Net in Shadow of the Beanstalk, an Android sourcebook for Genesys Roleplaying!”
Our focus today is looking at how The Net works in the world of Android – and with it, how hacking works. Because let’s be honest – that’s why we’re all jazzed about playing this game. With Shadow of the Beanstalk, FFG is expanding how the rules of the net work greatly from the basic rules in the Genesys Core Rulebook. Netrunning (or Running) is how players can get into trouble (and also where the adventure lies) within the setting. Sure, you can get killed in Meat Space, but there are fates worse than death in the Realm of the Digital…
Hacking in Android is an abstract process. Players aren’t sitting there writing code to inject or scripts to run…that’s a little too real. Instead the act of Hacking is treated more like an encounter they might have in Meat Space – “with rounds, turns, actions and maneuvers.” So if you’ve got the basics of how an encounter works already in the Genesys system, you’re 1/2 way there already.
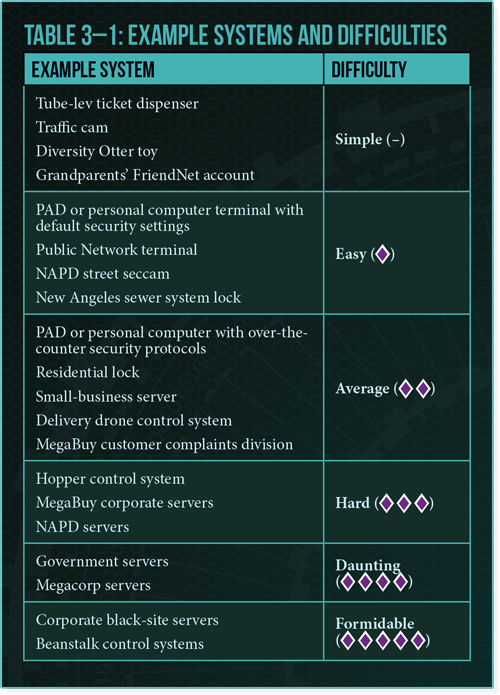
A run is really two steps when you break it down: Getting in and telling the system to do something. The “Getting in” part can be tough, depending on the system. Thankfully, FFG has a handy chart to show the difficulties you can expect with some in-game examples:
That’s not too bad, is it? No, it wasn’t – but now the challenge REALLY beings. You see, in Android, most systems you gain access to will have sub-systems. Those sub-systems are each designed to control a different purpose. If you’re hacking a buildings security system, for example, one sub-system might control the locks on the doors while another might control the alarms or the cameras – you get the idea.
Those sub-systems may or may not be available to you at first glance either. But one thing is known – which sub-systems are protected by ICE (that’s short for Intrusion Countermeasures Electronics). ICE is bad news for runners and if you’re familiar with the setting you’re aware that it can do all sorts of nasty things from simply booting you from the system, to triggering a trace to your location, to even causing deadly feedback to fry your brain.
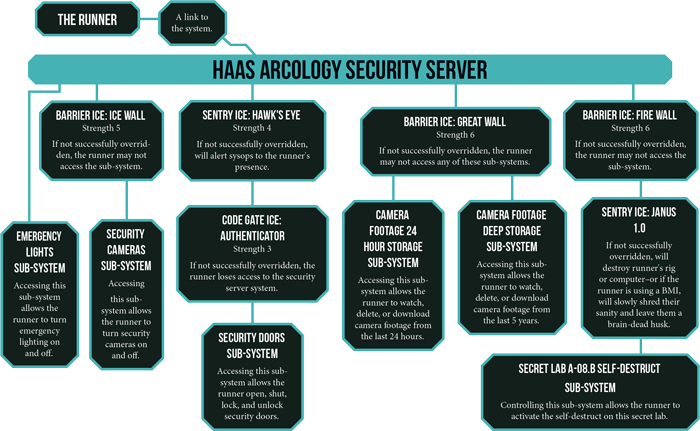 “An example system, detailing sub-systems and ice.”
“An example system, detailing sub-systems and ice.”
For fans of Netrunner, this structure should feel very familiar and honestly, this is very similar game play from a macro level. Runners are still probing systems and the “corp” (or GM) in this case may have dummy servers/sub-systems setup with traps for you to stumble into, but that is part of the fun!
A typical ICE will have a strength associated with it and an effect that can trigger when it is accessed. A runner can attempt to “Break the ICE” by making a check and comparing their result vs the ICE’s strength. That check is generated by making an average Computers check and the number of successes determines their strength. Now, there are additional ways to boost that result – by running Icebreakers of your own!
If an ICE is broken, it remains down until the end of your next turn. Now, if a sub-system is protected by multiple pieces of ICE, that means the players will have to have multiple runners or some other tricks to keep the ICE down. But be warned: ICE isn’t your only danger. There are also the System Operators known as Sysops.
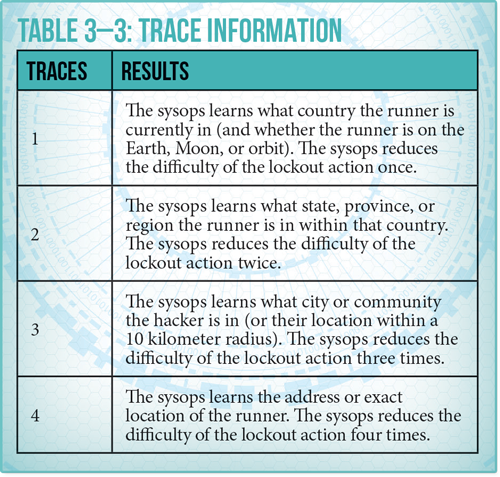
Sysops are basically the human (or sometimes non-human) employees that are there to monitor for intrusions on their network. When they spot an intrusion, they have two actions they can use to counter: A trace or a lockout. Getting tagged with a trace helps the Sysops find your exact real world location and can also make it easier for them to boot your from the system.
Avoiding a Trace requires a check for both the Sysops and the Runners – both make Computer checks. If the Sysop wins, the Runner is now Traced. If that keeps up, they can eventually use those to lower the difficulty of the Lockout check. This is a pretty cool way to play a game of Cat and Mouse!
Android is a fantastic setting to play around in if you’re a fan of Cyber-punk. So get ready to jack-in with the new Shadow of the Beanstalk coming soon from FFG!
Shadow of the Beanstalk $49.95
Shadow of the Beanstalk is a 256-page sourcebook for use with the Genesys Roleplaying System. In this book, you’ll find new rules for character creation, new weapons, equipment, and adversaries, new rules for running the net, information on the Android Universe, and advice for gamemasters running a campaign in the cyberpunk future of Android. All of this accompanied by beautiful art and elegant mechanics that can be used in any setting for the Genesys roleplaying system.
Don’t slip on the ICE…